How secure is Mobile Device Management anyway?
January 8, 2014 7 Comments
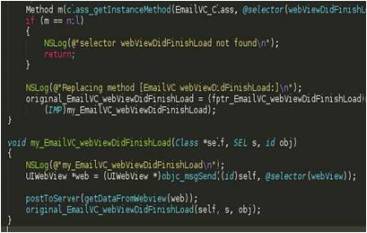 Researchers have successfully breached the Good Technology container. MDM software can only be as secure as the underlying operating system.
Researchers have successfully breached the Good Technology container. MDM software can only be as secure as the underlying operating system.
As the adoption of smartphones and tablets grows exponentially, one of the biggest challenges facing corporate IT organizations is not the threat of losing the device – likely owned by the employee – but the threat of a targeted attack stealing sensitive corporate data stored on these mobile devices. As a first line of defense, an increasing number of companies rely on Mobile Device Management software and Secure Container solutions to secure and manage corporate data accessed from these mobile devices. However, a recent analysis conducted by Lacoon Mobile Security – presented a few weeks ago at the BlackHat conference in Amsterdam – shows that the leading secure container solution Good Technology can be breached and corporate email stolen from Apple iOS and Android devices.
Lacoon CEO Michael Shaulov, spoke with me about the shocking results of this research and made it clear that no matter what MDM software you deploy, you are in danger. MDM and Secure Containers depend on the integrity of the host system. “Ask yourself: If the host system is uncompromised, what is the added value? If the host system is in-fact compromised, what is the added value? We’ve been through this movie before”, referring to the underlying endpoint management philosophy inherited from the previous PC era.
In their presentation “Practical Attacks against Mobile Device Management (MDM)”, Michael Shaulov and Daniel Brodie, Security Researcher, explain the details of how they penetrated the Good Technology container to exfiltrate sensitive corporate email – Good Technology did not respond to my request for comment:
Android 4.0.4 device – Samsung Galaxy S3:
1. The attacker creates a “two-stage” application which bypasses the market’s malicious app identification measures such as Google Bouncer or other mobile application reputation systems. The app is then published on Google Play or other legit Android appstores. By using the “two-stage” technique, the attacker can publish a seemingly innocent application and, once the victim installs the app, the app itself refers to the malicious code which is then downloaded.
2. The app exploits a mobile OS vulnerability which allows for privilege escalation. For example, the vulnerability in the Exynos5 chipset released in December 2012 that affects the drivers used by camera and multimedia devices.
3. The malware creates a hidden ‘suid’ binary and uses it for privileged operations, such as reading the mobile logs, as discussed in the next step. The file is placed in an execute-only directory (i.e. –x–x–x), which allows it to remain hidden from most MDM root detectors.
4. The malware listens to events in the ‘adb’ logs. These logs, and their corresponding access permissions, differ between Android versions. Note that for Android version 4.0 and higher root permissions are required in order to read the logs.
5. The malware waits for a log event that signifies that the user is reading an email.
6. The malware dumps the heap using /proc//maps and /mem. Accordingly, it can find the email structure, exfiltrate it and send it home – perhaps uploading it to an unsuspected DropBox account.
Apple iOS 5.1 device – iPhone:
Malware targeting iOS based devices needs to first jailbreak the device, and then installs the container-bypassing software.
1. The attacker installs a signed application on the targeted device, through the Enterprise/ Developer certificate. This may require physical access but there are known instances when this has done remotely.
2. The attacker uses a Jailbreak exploit in order to inject code into the secure container. The Lacoon researchers used the standard DYLD_INSERT_LIBRARIES technique to insert modified libraries into the shared memory. In this manner, their (signed) dylib are loaded into memory when the secure container executes.
3. The attacker removes any trace of the Jailbreak.
4. The malware places hooks into the secure container using standard Objective-C hooking mechanisms.
5. The malware is alerted when an email is read and pulls the email from the UI elements of the app.
6. Finally, the malware sends every email displayed on the device to the remote command and control server.
The analysis performed by the Lacoon analysts exposes the security limitation of the secure container approach. Shaulov believes that MDM provides management, not absolute security. It is beneficial to separate between business and personal data in a BYOD scenario. Its main use case is the selective remote wipe of enterprise content and Copy & Paste prevention.
Secure containers rely on different defense mechanisms to protect the corporate data. Generally these include iOS jailbreaking and Android rooting detection, prevention of the installation of applications from third-party markets in order to protect against malware and, most importantly, data encryption. However, these measures can be bypassed. On one hand there is a quite active community involved in jailbreaking/rooting efforts. On the other hand the jailbreaking/rooting detection mechanisms are quite restricted – see for example xCon, a free iOS app to defeat jailbreak detection. Usually, checks are performed only against features that signify a jailbroken/rooted device. For example, the presence of Cydia, a legit iOS app which allows the downloading of third party applications not approved by Apple, or the SU tool used on Android to allow privileged operations. More importantly, there are no detection mechanisms for exploitation. So even if the secure container recognizes a jailbroken/rooted device, there are no techniques to detect the actual privilege escalation.
MDM software and Secure Containers are supposed to detect jailbroken iOS and rooted Android devices but “they are dependent on the underlying operating system sandbox, which can be bypassed”, Shaulov says.
MDM not so secure after all
Sebastien Andrivet, Co-founder and director of ADVTOOLS, took a different approach to auditing the security of MDM products and performed a thorough analysis of the server components, such as the administrative console, and their communications with the mobile devices. I met Andrivet in London at the Mobile and Smart Device Security Conference 2012, where he presented the alarming results of his research. Among other, Andrivet found persistent cross-site scripting and cross-site request forgery vulnerabilities in two leading MDM solutions – he would not publicly disclose the names of these products but I saw the screenshots of the trace logs and spotted some of the leading brands mentioned in the Lacoon report.
Andrivet openly stated that, despite being marketed as security tools, MDM products are not “security products” and in fact not so secure after all. However, he is also a bit skeptical about the significance of the findings of the Lacoon research. “Frankly, it is not so easy to penetrate these products, especially on iOS”, says Andrivet. For example, to break into the Good container in the way described above, you need physical access to the device and the password. With an iPhone 4, it is still possible to break a 4-digit pass code. But it is not currently feasible to do the same with iPhone 4S and iPhone 5. Andrivet also observes that it is true that it is possible to repackage an existing iOS application and sign it with your own enterprise certificate. But to install it on the device, a victim will have to accept explicitly the installation of the certificate and then of the application itself. With social engineering, this might be possible, but definitely not so easy. Andrivet points out that the Lacoon researchers have not broken the secure container encryption. They found the information in clear somewhere else – i.e. in memory. What is important is that they found a way to get the data. How they did it (breaking or not the secure container) is not so important. They “breached” the container, even if they didn’t “break” it.
The truth is that MDM products, as any other piece of software in the world, suffer from actual security vulnerabilities. But the Lacoon research is making headlines based on old versions of these products. “The risk is to provide misleading information”, warns Andrivet. In fact, even military-grade spyphone products like FinFisher cannot infiltrate the most recent versions of mobile devices like iPhone 4S or 5 as it is far easier to attack an Android device than an iOS one.
MDM is no silver bullet
Mobile security is a complex topic, and there is no silver bullet. This is true of security in general and mobile is no different, says Ojas Rege, Vice President Strategy at MobileIron, one of the leading MDM software mentioned in the above researches. The challenge many organizations face is that they compromise user experience in the name of security. For mobile, that’s the kiss of death, because users will not accept a compromised experience.
The key is to divide the problem into two: reducing the risk of data loss from well-intentioned users and reducing the risk of malicious attack, continue Rege. The former is, for example, giving users a compelling but secure way to share files instead of using consumer-grade services such as DropBox. The latter is what these researches are really about. MDM is important as a baseline but a full security program is going to require a great deal of education as well. “Jailbreak/rooting is a cat and mouse game”, according to Rege. The reality is that these devices will always have personal use – no matter who owns them – so the chances of malicious software making its way into device are high. The level of sandbox security built into the core OS is a key determiner of what other protections might be needed and what the resulting risk might actually be.
The point about MDM not offering absolute security is a bit cavalier, according to David Lingenfelter, Information Security Officer at Fiberlink, another leading MDM product mentioned in the Lacoon research. Anybody in the security community who is touting or expecting absolute security has missed the point. Cybercriminals only have to be right once. While targeted attacks are definitely a reality, containers are designed for more than just stopping a targeted attack. They help with data leak prevention, blocking users from “accidentally” distributing corporate information through their personal apps.
For better or worse, corporate IT still has to work in the confines of a world dominated by compliance. Adding controls around corporate information by using containers helps risk and compliance teams show their auditors that they are taking what is in essence a consumer-grade device and adding corporate level processes to those devices, continue Lingenfelter.
Infection is inevitable
The lesson learned from trying to secure traditional endpoints may be applied here. The general consensus among the security community is that controls on endpoints are not sufficient anymore to protect from targeted attacks. We can expect the same in the mobile world.
“Infection is inevitable”, continue Shaulov. As demonstrated by our research, MDM and Secure Containers do not and cannot provide absolute security. These are certainly useful tools to separate between business and personal data. As such, they should be part of a baseline for a multi-layered approach. Quoting an RSA report, Shaulov argues that “mitigating the effects of malware on corporate data, rather than trying to keep malware off a device entirely, may be a better strategy”.
This new approach requires thinking outside of the box and the industry is now starting to wake up to this challenge and looking at the network level for threat mitigation. For example, solutions like FireEye, Damballa, Fidelis and Checkpoint – just to name a few – can look at different network parameters and aberrant behavior to detect a compromised device in the process of exfiltrating data. Parameters may be traffic to well-known C&C servers, heuristic behavioral analysis which signify abnormal behavior, sequences of events and data intrusion detection.
Lingenfelter agrees that approach to security has been, and needs to remain, an approach of layers. However, he warns that while other technologies that are based on heuristic style monitoring and detection of malicious activity have come a long way, they too are far from absolute security. Companies have to realize that most mobile technology has been designed for consumers. It has the security focus of consumer devices and applications, which is to make it as easy for the end user as possible. To say that there is going to be one single technology or approach to change this and make these devices have the security level of corporate devices is reckless. The true objective with mobile device security and management is to add on as much security, in layers, as possible without a significant impact on end user experience.
Have you deployed MDM to your mobile users? Do you trust mobile secure containers with your corporate data? How confident are you that your CEO’s iPhone is not jailbroken – or that it never was? Can you detect a compromised tablet spying on your company’s next board meeting?
NEXT: How Secure is Your Smartphone? Android, iOS, BlackBerry and Windows Phone Under Attack.




There are a number of issues raised by this post. They also happen to span various levels of tust and security needs. Let’s address them one by one.
* User cannot be trusted and extremely sensitive data:
— Do you trust the user not to use a jailbroken device for work or do anything obviously dangerous? Methods used in this article to hack are similar to someone downloading malware from unknown sources on their work laptop. A targeted email trojan is perhaps more effective and damaging on work PC, however, mobile adds an additional dimension. Solutions is usually to create layers of safeguards around sensitive information. Information segmentation and DLP systems are a couple of ways to address this. BYO is challenging in this scenario since there’s really no good way to protect data on a hacked PC or a jailbroken device against a targeted attack. Think Stuxnet 🙂
* Sensitive data but you trust the user and targeted attack is not a big concern:
— In this case a non-jailbroken mobile device presents a base platform that’s similar to work PCs. Complication is the dual use nature of mobile devices. MDM will prevent data loss in case of a lost device, however, it won’t prevent things like corporate data getting sync’ed to iCloud.
A container approach such as MobileSpan or Good will allow a safe separation of corporate apps and data on such devices. This approach protects from the data loss in transit and when it is stored on a device, even if the device is lost or stolen.
* Data not that sensitive
— Dropbox, anyone? 🙂
MDMs were not designed as security solutions to begin with. They are ASSET MANAGEMENT solutions. I think most people recognize that, which is why many MDM vendors are turning to add security technology like container and like wrapping to their offering, and why many companies start to evolve their BYOD solutions from MDM to more security-oriented solutions.
Secure containers are fairly secure, IMHO. Their weakness lies in the ability to deploy them in masses, not only to a small fraction of corporate-owned devices but also to the masses and quickly growing segment of personal devices. The danger is that if you don’t cover those devices, people would (for convenience reasons) start to leak data towards those devices.
There’s a third category of solutions not mentioned here which is GATEWAY solutions. At LetMobile, our Mobile Security Gateway would provide all the security services at the server side without relying on the device (which as indicated here may be rogue), and also does not leave data on the device (in case its stolen or attacked). The gateway also makes it easier to enforce powerful access control and DLP policies in real-time and per each access. Unlike the other solutions where once you downloaded data to the device its there (and possibly exposed), with LetMobile you can disallow same data in certain circumstances (e.g., when out of the country, or if the person was fired in the meantime, or if someone determines that certain data is too sensitive to be consumed on mobile devices).
What about hardware locking AND software protection some companies provide a hardware based solution. A SD card with FIPs compliant encryption for protecting Voice and text. Where does this play in the above equation?
Simply stresses the importance of actually protecting your data irregardless of the device utilized as an access point. Even if a solution is airtight, it will always come down to the fact that organizations are responsible for fortifying what is truly important. Of course, there is tremendous value to MDM/MAM solutions that move beyond security component. For instance, Aruba’s WorkSpace (j.mp/byodmam) focuses on empowering the user with an enriched app environment. BYOD should be able IT and the user base coming together to find ways to leverage todays tools in a way that improves the outcome.
Has your suggested solution-point been verified by a neutral third-party for software assurance needs? Every solution-point I have yet run across has been penetrated successfully during a penetration-test. I don’t understand how what you are suggesting is different.
“Move beyond the security component”… what does this mean?
My role at HP for the past 2 years has been in mobile app pen-testing and my experience and exposure to these MDM/MAM/MCM platforms indicates that they do not hold up in any particular environment — let alone a risky open/insecure/public WiFi.
I agree that multiple tools can be a solution if you know what the risks are because they are well-documented in an application security risk management portal.
Hey Andre, I appreciate your comment!
I believe the post clearly makes the point that no software is immune from security flaws and that a multi-layered approach is the way to go. If you could share additional data points based on your work at HP that would be much appreciated.
Thanks for stopping by.
Cesare
Great article! One of the issues that must be recognized by government and private sector is the need to physically sequester mobile devices in sensitive areas…board rooms, classified areas, etc. CMDs (commercial mobile devices) come readily available with video and audio recording capabilities. This means that in addition to roving the RF spectrum, someone with malicious intent, more blatantly espionage, could very easily obtain very sensitive information that can be gathered and stored for subsequent transmission to an ‘adversary.’ Technology is moving very quickly. And with that technology comes threats that are much more widespread and difficult to mitigate. Mobile device security, corporate and government, MUST employ a mult-layered, multi-disciplined approach. Mobile device security is not just an IT issue, it is not just a cyber issue. It is an issue for IT, Cyber, Physical and Facility. All of these disciplines must begin to work together to create a complete approach to what we currently call mobile device management!