Google Vault Makes Play for Mobile Security Hardware Space
June 2, 2015 Leave a comment
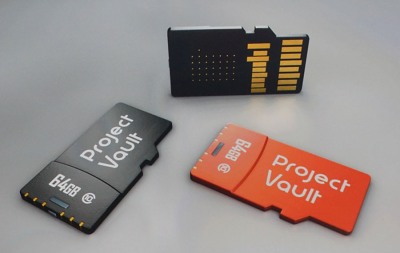 Last week Google made a splash with its latest futuristic tech offering: Project Vault. In essence, this mini-computer on an SD card is designed to enable secure authentication, communications and data storage on your smartphone or laptop. So what exactly is going on here? After years experimenting with Android, has one of the world’s biggest software companies finally admitted hardware level security is the way forward? And if so, what are the implications for enterprise and consumers? Read more of this post
Last week Google made a splash with its latest futuristic tech offering: Project Vault. In essence, this mini-computer on an SD card is designed to enable secure authentication, communications and data storage on your smartphone or laptop. So what exactly is going on here? After years experimenting with Android, has one of the world’s biggest software companies finally admitted hardware level security is the way forward? And if so, what are the implications for enterprise and consumers? Read more of this post