Smartphone Security Winners & Losers
October 9, 2012 Leave a comment
 Post based on my interview with Jeanne Friedman, content manager for RSA Conference.
Post based on my interview with Jeanne Friedman, content manager for RSA Conference.
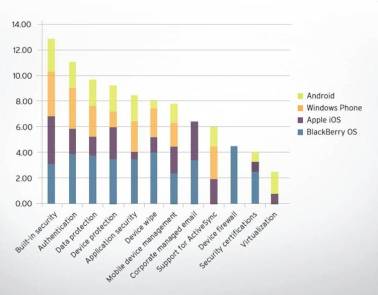
In the mobile space the BYOD trend is becoming a minefield for IT administrators. Many companies have experienced a data breach as a result of an employee owned device accessing the corporate network. When the stakes are this high, corporate IT needs to know which platforms to allow and which to refuse.
Android is the most popular mobile platform in the world. It is also the most vulnerable to attack and in fact the most exploited. Contrary to common perception, Apple mobile devices are not immune to security flaws. And in fact less secure than Android if users “jail break” their devices – to escape Apple’s control.



 Google recently announced Android 4.1 ‘Jelly Bean’ at its I/O conference in San Francisco. The latest flavor of the world’s #1 mobile OS promises better user experience and sexier UI. But does it really make any easier for IT to secure and manage those
Google recently announced Android 4.1 ‘Jelly Bean’ at its I/O conference in San Francisco. The latest flavor of the world’s #1 mobile OS promises better user experience and sexier UI. But does it really make any easier for IT to secure and manage those Where employees once enquired about private medical cover and company cars, now they may ask to work on their own iPhone or Android. It’s a perk of the job that can boost productivity, but implement your BYOD policy incorrectly (or even pretend it’s not happening) and it could cost you dear, say our experts
Where employees once enquired about private medical cover and company cars, now they may ask to work on their own iPhone or Android. It’s a perk of the job that can boost productivity, but implement your BYOD policy incorrectly (or even pretend it’s not happening) and it could cost you dear, say our experts